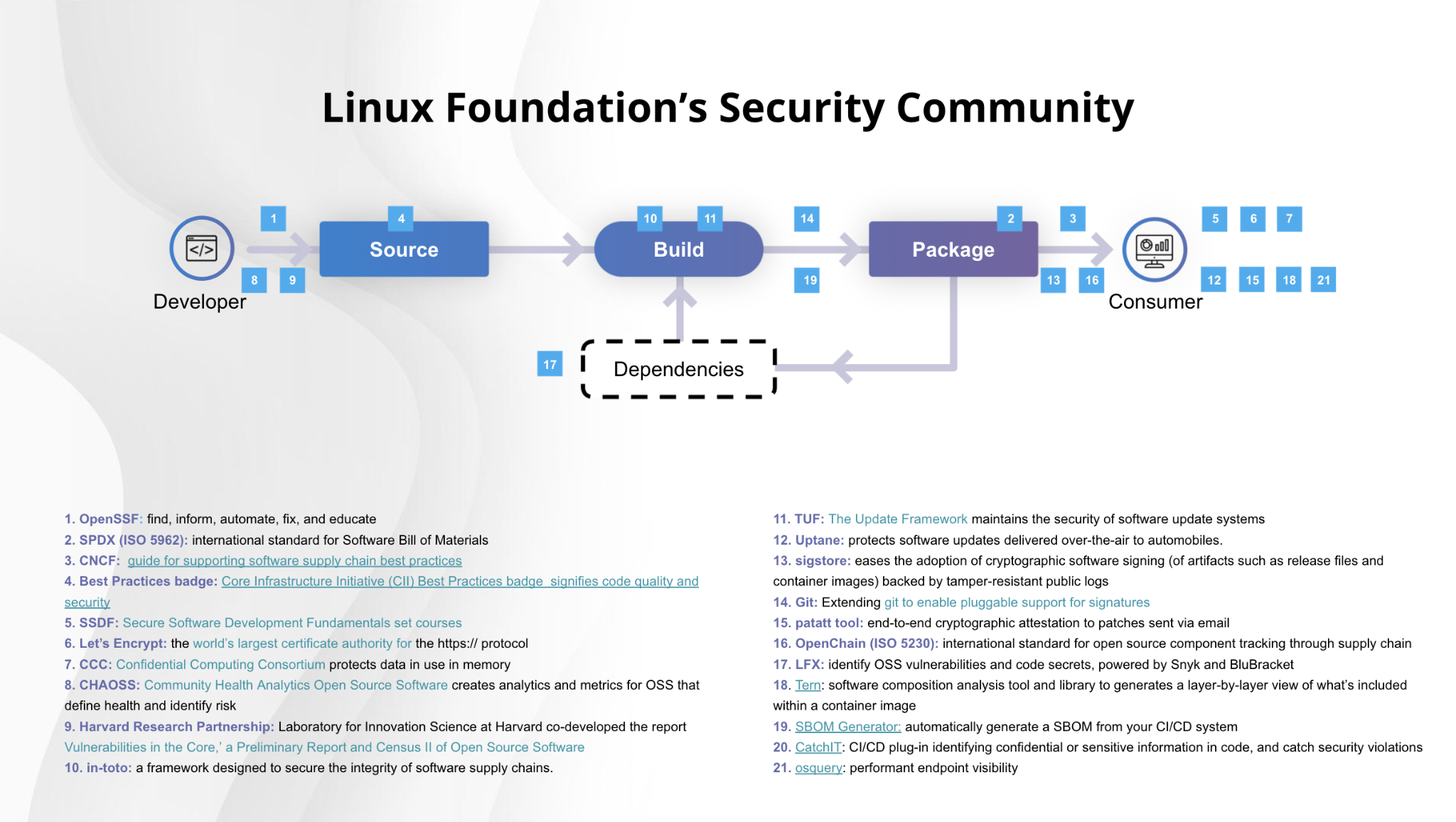
The World's Major Technology Providers Converge to Improve the Security of Software Supply Chains - Linux Foundation

The 2023 Report on Industrial Power-Generation Control Systems Security Software: World Market Segmentation by City: Parker Ph.D., Prof Philip M.: Textbooks: Amazon Canada

Installing and Configuring an nCipher Hardware Security Module (HSM) with FIM CM 2010 - TechNet Articles - United States (English) - TechNet Wiki