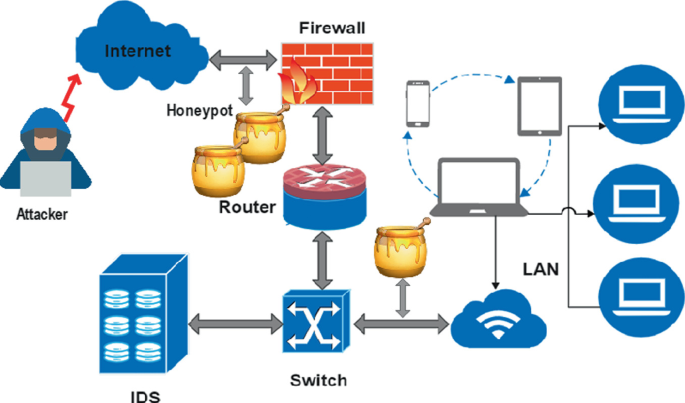
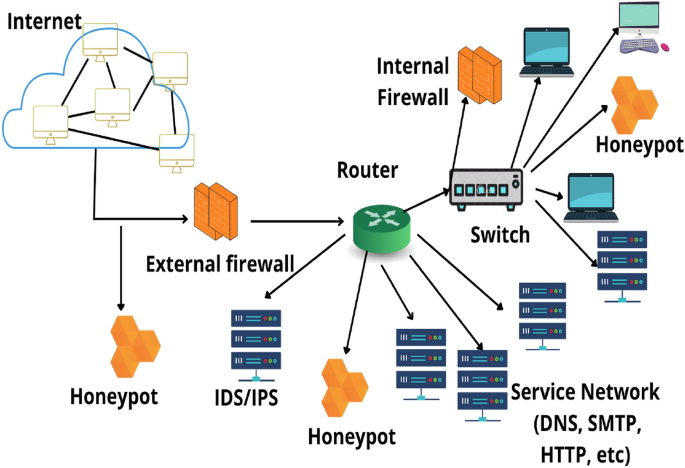
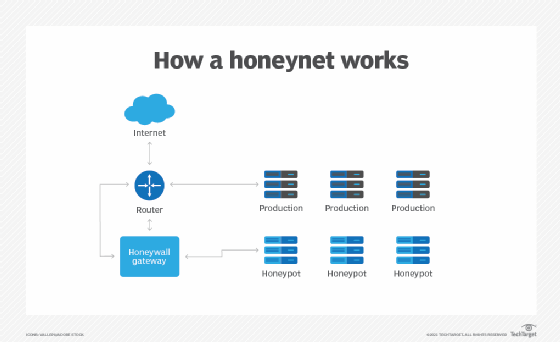
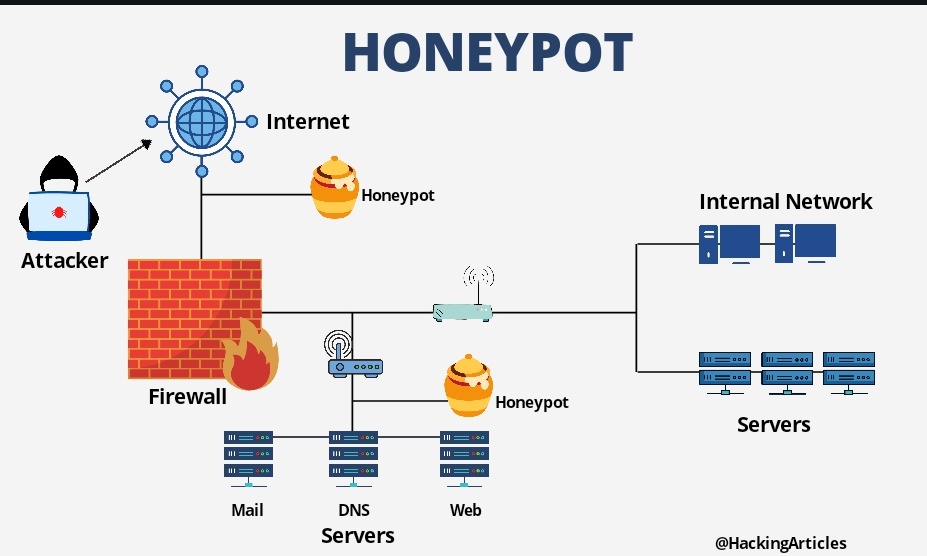
SoftSwitch: a centralized honeypot-based security approach using software-defined switching for secure management of VLAN networ
SoftSwitch: a centralized honeypot-based security approach using software-defined switching for secure management of VLAN networ









![PDF] Honeypot as the Intruder Detection System | Semantic Scholar PDF] Honeypot as the Intruder Detection System | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/2f0a86543b9c0c18f08311539237f74fe3601dfa/2-Figure1-1.png)